Penetration testing, also called pen testing, describes processes, tools, and services designed and implemented to simulate attacks and data breaches and find security vulnerabilities. You can run a pentest on a computer system, an entire network, or a web application.
The primary aim of a pentest is to identify vulnerabilities that attackers can exploit. There are various ways through which the identified vulnerabilities can be discovered. You can choose either manual pen tests, executed by a team of white hat hackers, or automated penetration testing, carried out by a software solution. Curious to learn more? Let’s dive in!
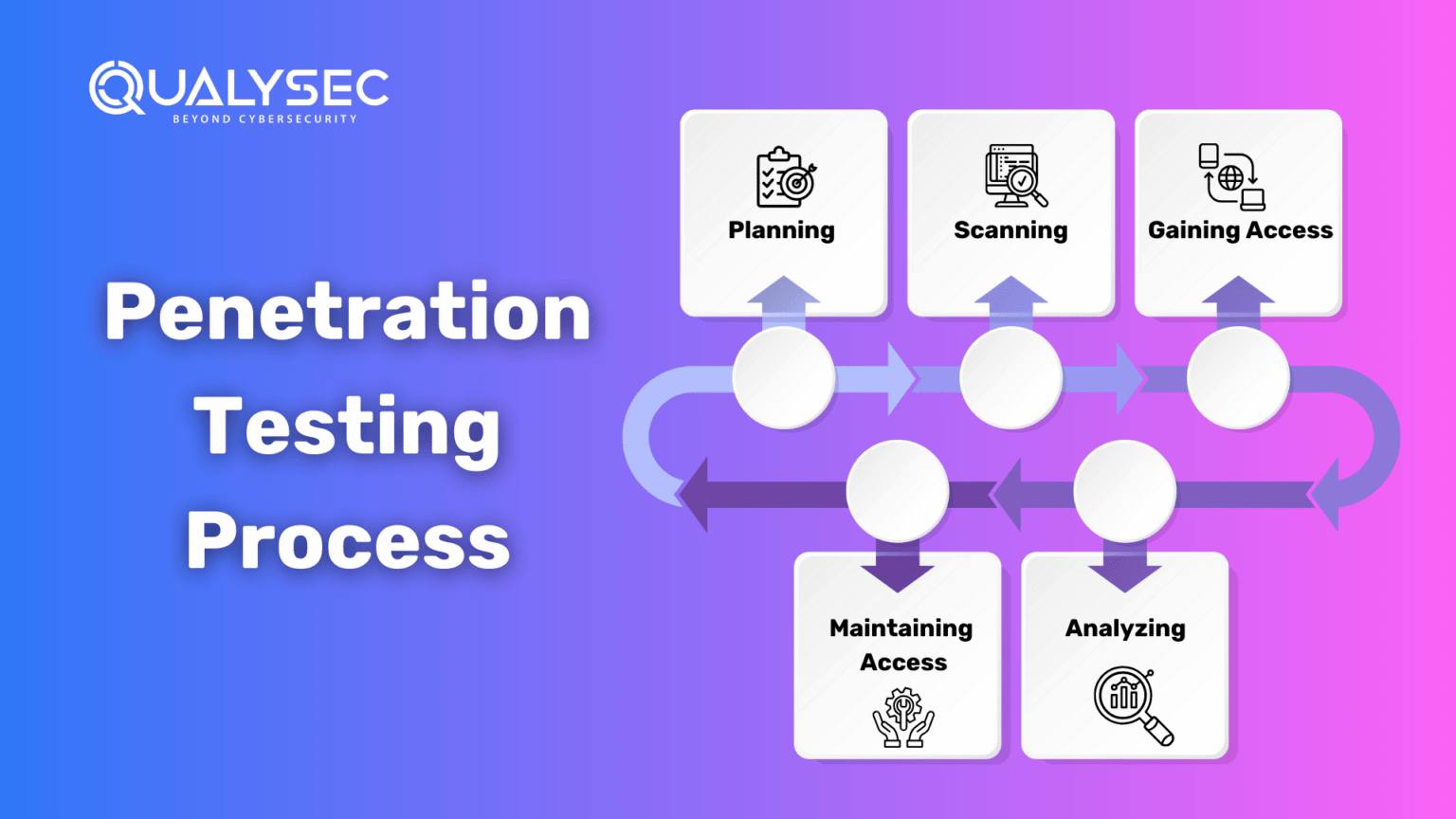
The penetration testing involves the following five fundamental stages:
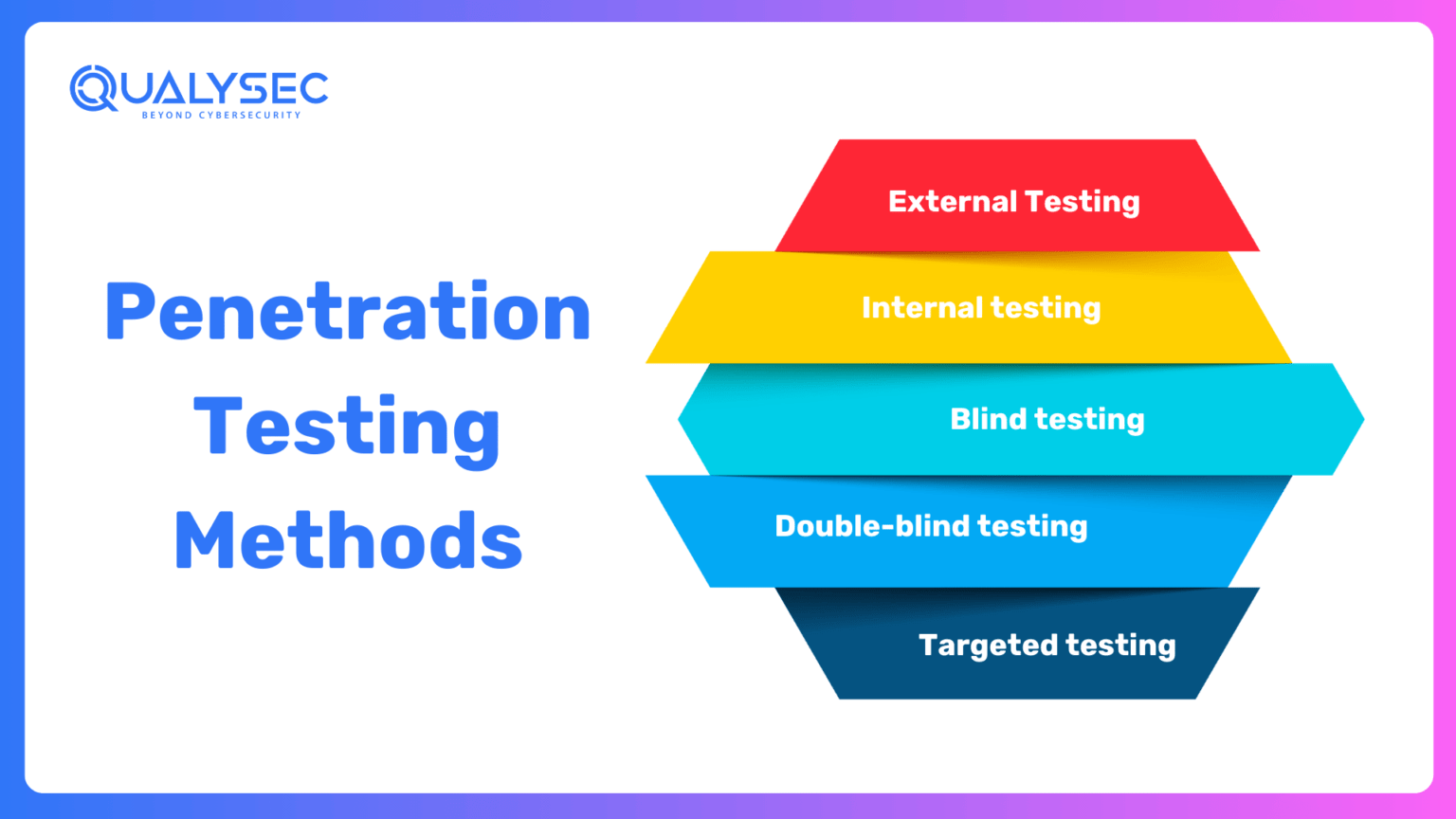
Let’s dive deeper into penetration testing methods that ethical hackers use to uncover vulnerabilities effectively.
The primary aim of a pentest is to identify vulnerabilities that attackers can exploit. There are various ways through which the identified vulnerabilities can be discovered. You can choose either manual pen tests, executed by a team of white hat hackers, or automated penetration testing, carried out by a software solution. Curious to learn more? Let’s dive in!
What are the Benefits of Penetration Testing?
Ideally, software and systems were designed to avoid hazardous security vulnerabilities in the design. A pen test shows how close it came to achieving that goal. Pen testing can help an organization in these ways:- Find weaknesses in systems
- Determine the robustness of controls
- Support compliance with data privacy and security regulations (e.g., PCI DSS, HIPAA, GDPR)
- Provide qualitative and quantitative examples of the current security posture and budget priorities for management
Penetration Testing Process

The penetration testing involves the following five fundamental stages:
- Planning: Identify and define the testing objective and scope. Collect intelligence information on the target, how the target works, and possible weaknesses.
- Scanning: Use the static and/or dynamic analysis of the network. This information allows the pentester to know how the application responds to various threats.
- Gaining Access: Identify the vulnerabilities in the target application using penetration testing techniques, such as cross-site scripting and SQL injection.
- Maintaining Access: Ascertain a criminal’s ability to retain access, owing to a vulnerability that has been exploited, and become privy to deeper forms of access.
- Analyzing: Assessing the penetration test’s results in a report describing vulnerabilities exploited, sensitive data accessed, and the timing of the response from the system during the penetration test.
Penetration Testing Methods

Let’s dive deeper into penetration testing methods that ethical hackers use to uncover vulnerabilities effectively.
